Governance, Risk Management and Compliance (GRC) is no longer simply a framework, but the power plant of a well-orchestrated cybersecurity strategy. Through the combined principles of governance, risk management, and compliance (GRC), organizations can link their IT ambitions with broader business goals and proactively model, mitigate, and respond to the associated risks, as well as to complex regulatory requirements.
Understanding GRC: Governance, Risk Management, and Compliance
Governance: The creation of policies, procedures, and frameworks to direct organizational function to meet business objectives and stakeholder requirements. Governance is further directed at the transparency and audibility of decision processes, and in that regard provides a firm foundation on the path to the realization of organizational objectives.
Risk Management: It encompasses the detection, assessment, and control of risk factors that interfere with the achievement of organizational objectives, such as those of information security and data privacy. It also deals with the preparation for the unexplainable (i.e., planning for contingency).
Compliance: It is noted that the organization has conformed to the law, regulation, standards, and internal rules to prevent legal liability and satisfy stakeholders. Compliance not only allows ethical work procedures to be developed but also helps enhance an organization’s public image.
The Importance of GRC in Cybersecurity
The integration of a GRC framework in cybersecurity is essential for the following reasons:
Holistic Security Approach: GRC is the integration of governance, risk management, and compliance into the workday, which aligns security programs with business goals and embeds security best practices into the organizational culture. This reduces silos and fosters collaboration.
Enhance Visibility: Leaders and organizational stakeholders need ongoing visibility into your cybersecurity efforts to ensure they are properly maintained. A well-implemented GRC framework establishes processes that provide clear visibility across the organization. This transparency allows for a proactive approach, ensuring that all potential threats are anticipated and managed effectively.
By embedding these processes, organizations can ensure that visibility is not just a one-time effort but an ongoing commitment. This continuous insight enables swift identification and response to risks, keeping stakeholders informed and confident in the organization’s security posture.
With GRC, organizations not only align their security efforts with broader business objectives but also achieve a level of transparency that is crucial for maintaining trust and accountability.
Centralized Control: By providing a centralized pane of glass, GRC platforms enable organizations to unify their cybersecurity and risk management efforts. This single interface simplifies the management of various security operations, allowing for a more efficient and cohesive approach. Decision-makers can monitor and operate protections seamlessly across the entire organization, ensuring that all aspects of security and compliance are aligned and visible.
Through this combination of cultural integration and centralized control, GRC frameworks not only enhance collaboration but also provide a more comprehensive view of an organization’s security posture, ultimately driving better strategic outcomes.
Risk Mitigation: Proactive identifying and mitigating risk through GRC to minimize cyber incident effects on business continuity. This also involves risk reduction due to emerging technologies like cloud computing and IoT.
Regulatory Adherence: As cybersecurity law grows in depth and scale, a GRC framework can guarantee organizations are complying, escape litigation, and maintain a good reputation. It also prepares organizations for audits and certifications.
By integrating compliance tasks and reviews into routine operations, a GRC framework helps reduce the likelihood of a breach in compliance. This seamless integration ensures that compliance becomes a part of everyday business activities, rather than a separate, daunting task.
Key Benefits of GRC Integration:
- Proactive Compliance: Regularly scheduled tasks and reviews ensure continuous monitoring and adherence.
- Operational Efficiency: Embedding compliance into daily operations streamlines processes and eliminates redundancy.
- Risk Mitigation: By closing compliance gaps, organizations are better equipped to avoid potential security breaches and regulatory penalties.
This comprehensive approach not only strengthens the cybersecurity posture but also enhances the organization’s ability to respond effectively to evolving regulatory demands.
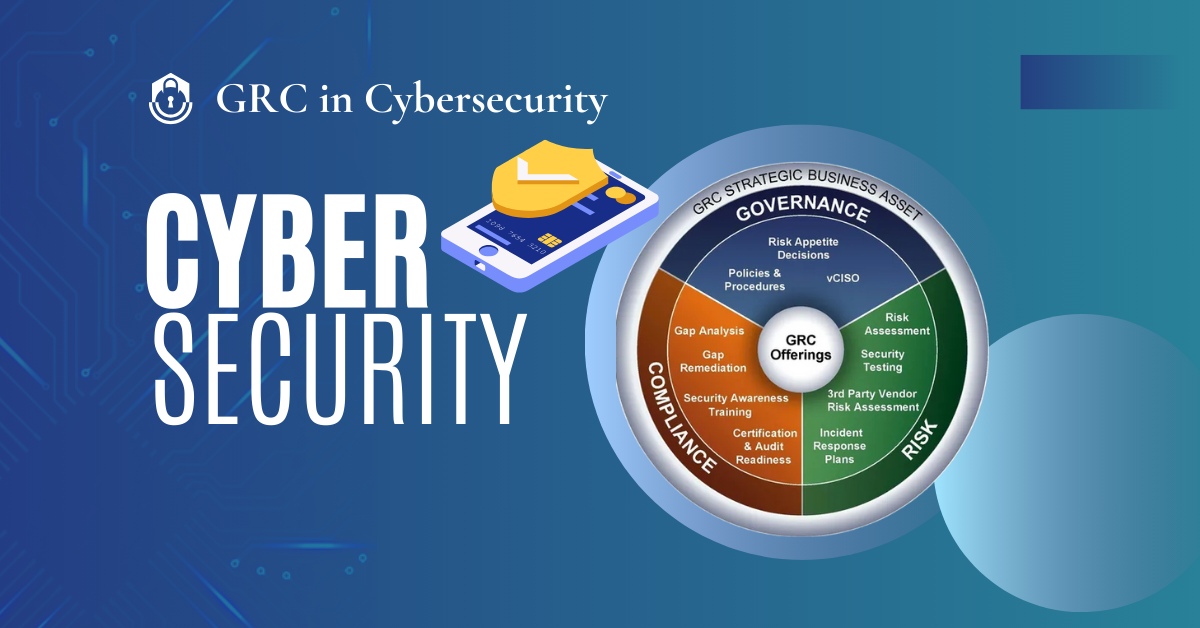
Components of GRC in Cybersecurity
Governance
Effective governance in cybersecurity involves: Effective governance in cybersecurity involves:
Policy Development: Develop comprehensive security policies, including putting forward an acceptable use policy or access controls and data protection rules and regulations) that are appropriate to organizational requirements. Policy rules are advised to be periodically reviewed and adjusted to match threat landscape changes.
Leadership Commitment: Making sure the most senior management is involved in and champions cybersecurity efforts that maintain a security-aware culture. Leadership engagement guarantees that cybersecurity will be given the time and attention it deserves.
Accountability Structures: Defining security roles and responsibilities in the company. This involves the appointment of a Chief Information Security Officer (CISO) to lead security activities.
To ensure a robust Governance, Risk, and Compliance (GRC) program, it’s essential to establish clear roles and responsibilities across the organization. Here’s a breakdown of key positions and their contributions:
- Board of Directors: Central to the overarching GRC strategy, the board sets the direction for compliance, determining necessary standards and aligning the GRC strategy with business objectives.
- Chief Financial Officer (CFO): Holds primary responsibility for the success of the GRC program, reporting results to the board, and ensuring financial compliance.
- Operations Managers: These department leaders own processes and are responsible for risk management and compliance within their areas, ensuring alignment with the overall GRC strategy.
- Department Representatives: As activity owners, these team members integrate compliance and risk management tasks into their workflows, ensuring seamless operations.
- Contract Managers: Focused on managing interactions with vendors, ensuring all risk management and compliance measures are observed.
- Chief Information Security Officer (CISO): Beyond leading security activities, the CISO defines information security policies, designs risk assessments, and develops security protocols.
- Data Protection Officer (DPO) or Legal Counsel: Develops data privacy goals based on legal requirements, implements privacy policies, and assesses their effectiveness to ensure compliance.
- GRC Lead: Oversees the execution of the GRC program, working closely with the executive team and maintaining the organization’s security controls library.
- Cybersecurity Analysts: Implement and monitor cybersecurity measures, ensuring they align with the GRC program and business objectives.
- Compliance Analysts: Monitor the organization’s adherence to necessary regulations and standards, identifying and mitigating any compliance gaps.
- Risk Analysts: Execute the risk management program, serving as a resource for identifying, mitigating, and monitoring risks across various departments.
- IT Security Specialists: Implement security controls within the IT system, coordinating efforts with cybersecurity analysts to maintain a secure infrastructure.
This structured approach to role definition not only enhances accountability but also ensures that all aspects of the GRC program are effectively managed and integrated throughout the organization.
Risk Mitigation Strategies and Automation Techniques
In today’s fast-paced digital landscape, automating risk management processes is crucial for maintaining robust security and operational efficiency. Automation not only enhances accuracy but also streamlines workflows, allowing organizations to focus on strategic initiatives.
Risk Mitigation Strategies: The establishment of controls and measures to mitigate identified risks to an acceptable extent. Examples are the deployment of firewalls, penetration testing, and data encryption.
To effectively automate risk management, consider the following steps:
- Identify Key Risk Areas: Begin by pinpointing the critical areas in your organization that require immediate attention. Automation tools can help in continuous monitoring and detection of potential vulnerabilities.
- Leverage Advanced Technologies: Utilize artificial intelligence and machine learning to predict risks and automate routine assessments. These technologies can analyze vast amounts of data quickly, identifying patterns that might be missed manually.
- Integrate with Existing Systems: Ensure that your automation tools seamlessly integrate with existing IT infrastructure. This integration allows for real-time data sharing and more effective risk management.
- Regular Updates and Testing: Automated systems require regular updates to stay effective. Implement periodic testing and updates to ensure that your risk management strategies remain robust against evolving threats.
- Training and Awareness: Even with automation, human oversight is essential. Train your team to understand and manage automated systems effectively, ensuring they can respond swiftly to any alerts or changes.
By combining these automation techniques with traditional risk mitigation strategies, such as firewalls, penetration testing, and data encryption, organizations can create a comprehensive defense mechanism. This synergy not only mitigates risks effectively but also optimizes resource allocation, enhancing overall operational resilience.
Compliance
Compliance in cybersecurity entails: Compliance in cybersecurity entails:
Regulatory Awareness: Keeping abreast of relevant laws and standards that are relevant to the organization, e.g., GDPR, HIPAA, or CCPA.
Audit Readiness: Preparing for a compliance audit requires a strategic approach to ensure all bases are covered. Here’s a comprehensive guide to help you navigate the process smoothly:
- Documentation and Evidence Collection: Maintaining documentation and evidence of compliance efforts to demonstrate adherence during audits. This may involve reports from vulnerability scans and training logs.
- Internal Review and Assessment: Conduct a thorough internal review of your current compliance status. Identify any gaps in compliance and address them promptly to avoid surprises during the audit.
- Training and Awareness: Ensure that all staff members are aware of compliance requirements and are adequately trained. Regular training sessions and updates can help keep everyone informed and prepared.
- Organizational Communication: Establish clear lines of communication within your organization to facilitate the flow of information. This ensures that any compliance issues are quickly identified and resolved.
- Checklist Utilization: Develop a checklist that outlines all necessary steps and documentation needed for the audit. This checklist should include timelines and responsible parties for each task, providing a clear roadmap for preparation.
By implementing these strategies, you’ll be well-equipped to face any compliance audit with confidence and clarity.
Implementing GRC in Your Organization

To effectively implement GRC and develop a comprehensive compliance program:
Assess Current State: Start by evaluating your current governance, risk management, and compliance practices to pinpoint weaknesses. This involves examining existing cybersecurity policies and risk management approaches. Additionally, identify specific compliance requirements pertinent to your industry and regulatory environment.
Define Objectives: Establish specific objectives for the GRC implementation to support business aims. Goals should include achieving regulatory compliance, lowering cyber risk, and improving incident response. Compliance programs, also focus on developing a culture of compliance and ensuring adherence to legal obligations.
Develop a Roadmap: Create a detailed plan outlining steps, timelines, and resources required for implementation. The roadmap should prioritize high-impact areas and detail the development of compliance policies, procedures, and training programs for employees.
Leverage Technology: Utilize GRC tools and platforms to streamline processes and improve efficiency. For example, employ software that provides automated compliance monitoring and risk evaluation. Consider tools that offer features like real-time reporting and alerts to ensure ongoing compliance.
Establish a Compliance Team: Form a dedicated team responsible for overseeing compliance efforts. This team should include representatives from key departments and be tasked with maintaining up-to-date knowledge of regulatory changes.
Monitor and Improve: Regularly monitor the effectiveness of the GRC framework and make necessary improvements. This involves periodic audits, reintegration of stakeholder feedback, and continuous risk assessments to ensure compliance measures remain effective and relevant.
Conduct Training and Awareness Programs: Implement training sessions to educate employees about compliance requirements and the importance of adhering to policies. Regular training helps to cultivate a culture of compliance throughout the organization.
By integrating these steps into your overall strategy, you can develop a robust compliance program that not only meets regulatory requirements but also enhances your organization’s resilience and reputation.
Challenges in GRC Implementation
Organizations may face several challenges, including Organizations may face several challenges, including:
Complexity: Implementing GRC across different divisions can be complex because differing processes and requirements exist. Addressing this requires cross-departmental collaboration and standardized procedures. [For example] The IT and legal departments need to collaborate to guarantee compliance with data privacy laws.
Resource Constraints: Limited financial and human resources can pose significant challenges to successful implementation. This can be achieved by organizations focusing on key areas and by requesting external inputs where required.
Resistance to Change: There can be reluctance on the part of employees to use new processes if change processes and communication are not adequate. Offering incentives and clear benefits can help mitigate resistance.
Benefits of Effective GRC Practices
Implementing GRC effectively offers numerous advantages:
Enhanced Decision-Making: Provides a systematic way to bring IT into line with business needs. For example, an integrated risk management dashboard can help executives make informed decisions faster, such as prioritizing investments in cybersecurity tools.
Cost Reduction: Streamlines processes, reducing redundancies and associated costs. Automated compliance checks can save time and resources compared to manual audits.
Improved Security Posture: Actively mitigates risks thereby potentially creating a stronger cyber defense. A strong security position is also a factor that can help to build both customer trust and the business’s name.
Reduce Third-Party Risk: By incorporating rigorous vendor vetting and selection practices, GRC reduces the risk of third-party tools becoming a gateway for unauthorized access to sensitive data. This proactive approach safeguards your data integrity.
Improve Collaboration: GRC fosters seamless collaboration across departments. Aligning everyone’s responsibilities and preventing miscommunication, ensures that cybersecurity tasks are effectively managed and nothing falls through the cracks.
Close Compliance Gaps: Through regular integration of compliance tasks into daily operations, GRC minimizes the risk of non-compliance due to changing software updates or practices, thus maintaining regulatory standards consistently.
Enhance Visibility: GRC frameworks enhance the transparency of your cybersecurity measures. By establishing ongoing visibility processes, leaders and stakeholders can ensure that security protocols are consistently upheld and understood across the organization.
Centralize Security and Compliance Operations: GRC brings together cybersecurity implementation and risk management under a unified framework, creating a centralized view that simplifies the management of security measures and compliance efforts.
By weaving these elements together, GRC not only strengthens the security infrastructure but also ingrains a culture of security mindfulness within the organization. This comprehensive approach positions businesses to better navigate the complexities of modern cybersecurity landscapes.
GRC Use Cases
Practical applications of GRC in cybersecurity include:
Regulatory Compliance: Maintaining compliance with standards e.g., GDPR, HIPAA, or PCI-DSS. Automated tools can track compliance requirements and generate reports.
Incident Response: Developing protocols for efficient, rapid, and timely security breach response. This includes creating playbooks for common attack scenarios.
To build an effective incident response plan, follow these critical steps:
- Identify and Prioritize Assets: Begin by cataloging all digital assets and identifying those most critical to your operations. Understanding what needs protection is the first step in preparing for potential incidents.
- Establish a Response Team: Assemble a dedicated team with defined roles and responsibilities. This team should include IT professionals, legal advisors, and communication experts to manage all aspects of an incident.
- Develop Detailed Playbooks: Create step-by-step playbooks for common attack scenarios like phishing, ransomware, or data breaches. This ensures your team can respond quickly and consistently when an incident occurs.
- Implement Detection Mechanisms: Invest in robust monitoring tools to detect unusual activities on your network. Early detection is crucial for minimizing the impact of a security breach.
- Conduct Regular Training and Simulations: Regularly train your response team and conduct simulations to ensure readiness. This practice helps identify weaknesses in your plan and improves team coordination.
- Review and Update Plans Regularly: An incident response plan is not static. Regular reviews and updates are essential to adapt to new threats and changes in your organization.
By integrating these steps with established protocols, your organization can enhance its ability to manage and mitigate security breaches effectively.
Vendor Management: The evaluation and control of third-party risk of the supply and alliance partners. Periodically auditing vendors can guarantee compliance with security and compliance standards.
To further enhance security, incorporate practices for vetting and selecting vendors from the start. By doing so, you significantly reduce the likelihood of unauthorized access to your data through third-party tools. This proactive approach ensures that only vendors who meet stringent security criteria are integrated into your systems, fortifying your cybersecurity defenses.
In essence, adopting a comprehensive GRC framework not only involves ongoing audits but also emphasizes prudent vendor selection, creating a robust barrier against potential cybersecurity threats.
How to Implement a GRC Strategy
Establish Leadership Support: Commitment from leadership to lead the GRC effort. It can be done by workshops, providing projections of Return on Investment, or having GRC goals in line with business items.
Form a Cross-Functional Team: Include representatives from various departments to ensure comprehensive coverage. Bringing together a diverse team guarantees a variety of perspectives are represented and valued.
Conduct a Risk Assessment: Identify and prioritize risks to address. This should also, especially, be considered for new threats such as ransomware, and insider threats.
Develop Policies and Procedures: Develop rules under the recognized threats and compliance standards. Policies should be readily available and written in plain, concise terms.
Implement Controls: Take action to prevent risks and compliance. Examples include multi-factor authentication and data loss prevention tools.
Train Employees: Educate staff on their roles within the GRC framework. Interactive training sessions and simulations may enhance the level of engagement and retention.
Monitor and Review: Continuously monitor the effectiveness of the strategy GRC and update it if necessary. Regular feedback sessions with stakeholders can provide valuable insights.
Conclusion
Integration of Governance, Risk Management, and Compliance into cybersecurity activities, however, remains critical to the success of organizations that seek to secure their digital information resources, maintain regulatory compliance, and drive business goals. A robust GRC framework not only mitigates risks but also fosters a culture of accountability and continuous improvement, enabling organizations to thrive in an increasingly complex cybersecurity landscape.
No responses yet