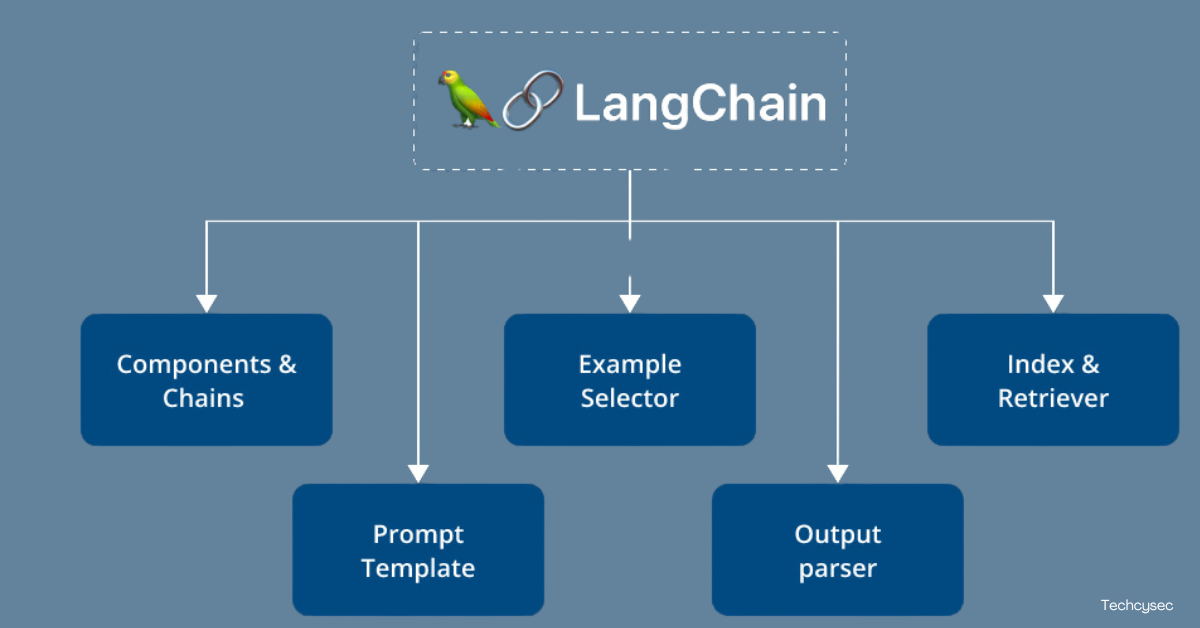
Generative AI: Building LLM Applications with LangChain Framework
The functionality of machines making human-like content, particularly text, images, etc., has become a different thing, thanks[…]

Is Cybersecurity Hard? Let’s Break It Down (And How to Get Started)
The domain of cybersecurity is rather widely discussed currently, especially when we relate it to the digital[…]

DeepSeek vs ChatGPT: Open-Source & Affordable AI
DeepSeek AI has gained traction as an important member of the artificial intelligence community, in fact, one[…]

What is Cyber Background Checks
As per the recent trend, the digital traces we live behind, contribute a great deal of impression on[…]

The Certified Information Systems Security Professional (CISSP) Certification
A Certified Information Systems Security Professional (CISSP) is a respected certification in the domain of cybersecurity that[…]

Does Cybersecurity Hire Often?
The cybersecurity career is still rapidly expanding because of a continuously growing number of cyberattacks. Organizations need[…]
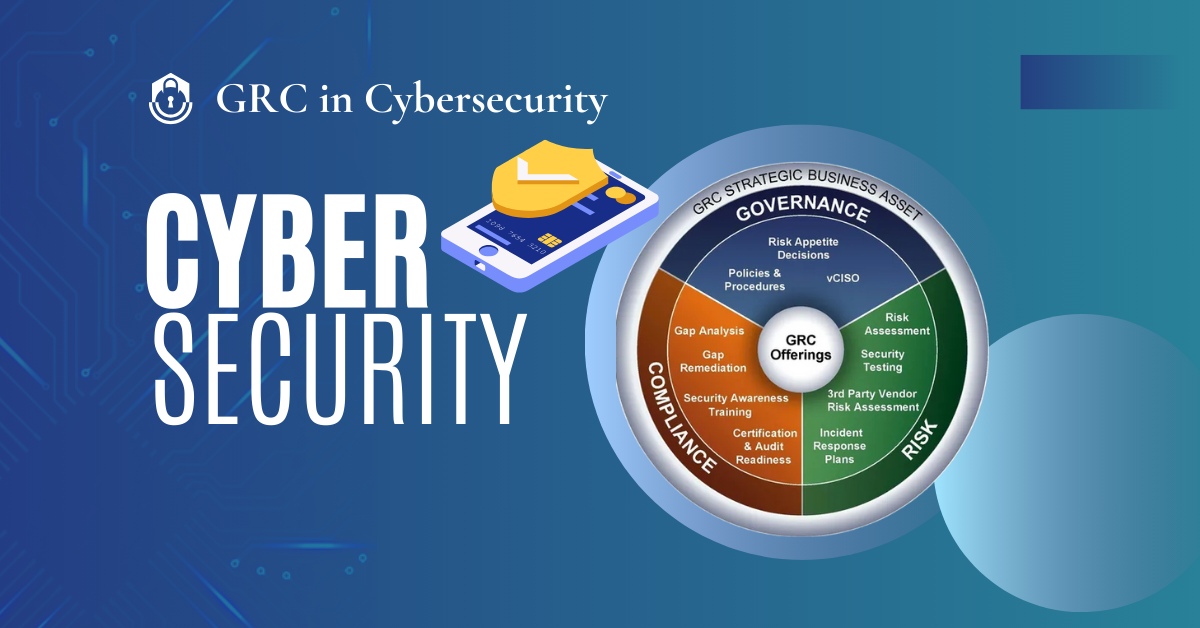
Mastering Cybersecurity with GRC: Governance, Risk & Compliance
Governance, Risk Management and Compliance (GRC) is no longer simply a framework, but the power plant of[…]
Character AI: Everything You Need to Know
Introduction: Character AI (referred to as Beta Character AI) is a new prominent development within the field[…]
